Update: myBasis have changed their API, breaking the scripts below.
– January 2014
Tested and being used on Debian Wheezy. Script download
These scripts will retrieve your biometric data from MyBasis for the last hour. The results can be checked from a Nagios host file, using the downloaded plugin.
First you must find your BasisID, and set the ‘uid‘ value in get_basis_data.py
Execute the script ‘get_basis_data.py‘ from crontab, setting it to run no more frequently than every 15 minutes (Basis data is uploaded once every 15 minutes, at best). It is recommended to run the script in crontab as user nobody.
Basis data is now written to several files in /tmp
The file nagios_plugins/usr/lib/nagios/plugins/check_basis should be copied to directory: /usr/lib/nagios/plugins/ on the Nagios Server, and permission set to 0755 (-rwxr-xr-x).
The file nagios_plugins/etc/nagios-plugins/config/basis.cfg should be copied to directory: /etc/nagios-plugins/config/ on the Nagios Server.
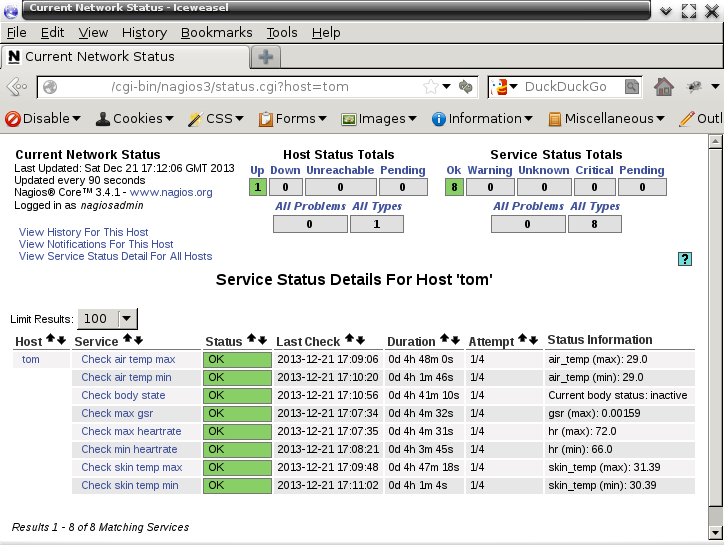
The commands check_basis and check_basis_body may be called from a standard Nagios Host configuration file. Example:
define service{
use generic-service
host_name tom
service_description Check max heartrate
check_command check_basis!hr!max!110!130
}
Substitude ‘hr‘ for ‘gsr‘, ‘air_temp‘ or ‘skin_temp‘. ‘max‘ may be replaced with ‘min‘. The other two values set the warning and critical thresholds.
The other command ‘check_basis_body‘ takes no parameters and is only informative.
You can now be monitored by your NMS!